That was so yesterday. To make things worse, banking institutions blinded by greediness had resorted to squeeze every penny of profits by cutting off security guards manning ATM machines. They depend on merely CCTV cameras and alarm systems as their only defence. Hence, the latest ATM thefts methodology has left the authorities head scratching. So far, 14 bank branches belonging to Affin Bank, Al Rajhi Bank and Bank Islam were reportedly hacked into by a Latin American gang which made off with over RM3 million.

Malaysian Bukit Aman Commercial Crime Investigation Department chief Comm Mortadza Nazarene revealed that the suspects used a computer malware known as “ulssm.exe” to hack into the ATMs. The suspects were found to have opened the top panel of the machine without using a key and inserted a compact disc into the machine’s processing centre which caused the ATM’s system to reboot.

The sophisticated gang then used a keyboard to hack into the system and take out money. According to systems engineer of a bank – up to 40 notes could be taken out in a single transaction using the method. Needless to say, the absence of security guard ease the gang’s task, so much so that they could go for a spa or coffee session before coming back to collect their loots.

But is this something very new as if it was invented yesterday? Actually, the risk of using such malware or to be precise – ATM trojan horse - was published back in May 2014. What this means is, somebody had already done that using the same method somewhere in the world. Unfortunately, the police were too busy carrying orders from their politician masters arresting opposition for petty and silly seditious allegations.
As far back as 2010, computer security experts have shown how ATM machines can be hacked to spit money, using hardware kit that cost less than US$100 to make. And the ATM’s motherboard is only protected by a door, of which you can buy the “universal key” online (*grin*). You can then used a USB port on the motherboard to upload your own software (stored in your USB stick), which changed the device’s display, played a tune, and made the machine spit out money.



So, how did the high-tech Latin American gang hacked and stole RM3 million (US$920,000; £560,000) in a couple of nights? It all started with Microsoft – they stopped supporting Windows XP operating system after 8th April, 2014. In other words, even if the ATM trojan horse was discovered one day after the end-of-support date, Microsoft will not release any security patches to plug the threat, period.

The problem is there are up to 95% ATM machines still running on Windows XP. Again, due to cost and profit, banking institutions prefer to close one-eye and pretend as if their ATMs were as secured as the Alcatraz. In the case of Malaysian ATM thefts, the Latin Americans could most likely infected their compact disc with “Backdoor.Padpin” trojan horse. Once the CD is inserted, the ATM reboots and execute the trojan horse, which create the following file:
- [PATH TO THREAT]\ulssm.exe
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\”ulssm.exe” = “[PATH TO THREAT]\ulssm.exe“
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\”ulssm.exe” = “[PATH TO THREAT]\ulssm.exe“
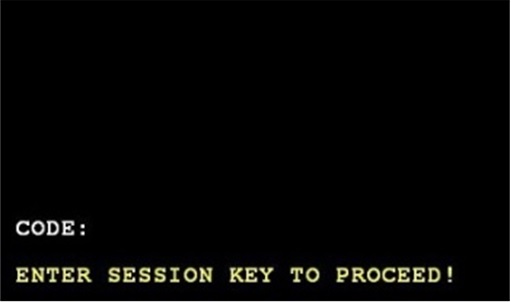
The Trojan can delete itself if it fails to gain control of the PIN pad or dispenser. It runs in the background until a specific code is entered on the ATM’s PIN pad. Finally, it then opens a back door on the ATM running Windows XP, allowing an attacker to perform the following actions:
- Display cassette information such as bills left, denomination and total amount per cassette
- Dispense money from the compromised ATM
- Select which cassette the ATM dispenses money from
- Temporarily disable the local network to avoid triggering alarms when withdrawing money
- Extend the duration of the session in order to continue stealing money
- Delete the Trojan from the compromised ATM
There’s also another famous trojan horse – Backdoor.Ploutus – which was discovered in 2013 to hack ATMs in Mexico. Amazingly, this Ploutus trojan allows cybercriminals to simply send an SMS to the compromised ATM, then walk up and collect the dispensed cash. Here’s how it works:
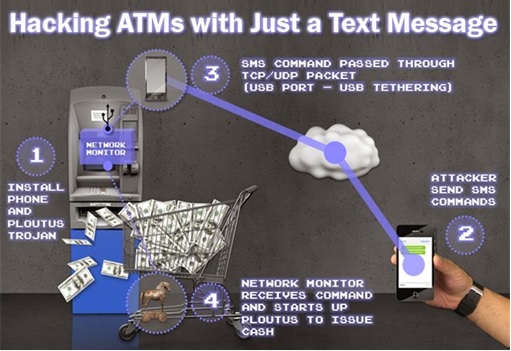
- Connect a mobile phone to the machine with a USB cable and install Ploutus Trojan.
- Sends two SMS messages to the mobile phone inside the ATM.
- SMS 1 contains a valid activation ID to activate the trojan horse
- SMS 2 contains a valid dispense command to get the money out
- Mobile attached inside the ATM detects valid incoming SMS messages and forwards them to the ATM as a TCP or UDP packet.
- Network packet monitor (NPM) module coded in the trojan receives the TCP/UDP packet and if it contains a valid command, it will execute Ploutus
- Amount for Cash withdrawal is pre-configured inside the trojan horse itself.
- And voila, the hacker can collect cash from the hacked ATM machine.

At the moment, it’s not sure if the Latin American gang used the “Padpin” or “Ploutus” trojan, or another type of variant. If police’ revelation is true, and not just another marketing stunt to convince the public about their efficiency, then the first method could be used. But that does not explain the phone SIM card usage during the ATM hacking operation, as what the police have claim.

Whichever the method used, the Latin American gang did one huge mistake – they forgot to erase their foot trail by deleting their trojan from the ATMs hacked and robbed. Perhaps they were too excited and surprised with the lack of banking security in this country. Either way, the fact that no security guard was deployed to this “goldmines” can only means one thing – the hacking spree is going to continue (*tongue-in-cheek*).
http://www.financetwitter.com/2014/09/here-is-how-malaysian-atms-were-hacked-of-rm3-million-by-latin-americans.html

No comments:
Post a Comment